AD Internal Hybrid
AD/Internal User Source
The Active Directory/Internal Hybrid authentication profile type combines the Internal User Source type with the Active Directory User Source type. Active Directory is used to find all of the users, and to check their credentials when they attempt to log in. However, it allows assigning of roles, contact info, and other meta-information about a user through Ignition, then stores all this information as if it were an Internal User Source. This way, Active Directory can be consulted to see if a username/password is valid, but the management of roles does not require coordination with your IT Department, who typically controls the Active Directory system. This "best of both worlds" approach is popular for many users of Active Directory.
The AD/Internal Hybrid User Source is partially manageable in Ignition. Users cannot be added or removed, and their usernames and passwords cannot be changed. This is because this information resides in Active Directory, not within Ignition. Other information, such as user roles, contact info, schedules, are manageable in Ignition.
Before you can use the User Management component to manage roles, contact info, etc., you first have to go into Gateway Settings, and mark the checkbox to 'Allow User Admin.' This allows for the administration of the Gateway's system user source from the Designer and the Client. Unless this is enabled, the Vision Module's User Management component is prevented from modifying the Gateway system's user source.
Property Reference
This User Source shares many properties with the AD User Source. Please see the Active Directory Authentication page for a list of properties.
Creating an AD/Internal Hybrid User Source
To set up an AD/Internal Hybrid User Source, you must specify the host that is acting as your primary domain controller. You can also use a secondary domain controller in case the primary is unavailable. You'll also need to specify the name of the domain and credentials for the Gateway itself to use for authentication for when it queries the list of roles.
When using AD/Internal Hybrid User Source, you may need to consult with your internal IT Department to get the required information to complete your user source setup.
-
On the Gateway webpage, under the Platform tab, go to Security > User Sources. The User Sources page will be displayed. Click Create User Source +.
-
Choose the AD/Internal Hybrid authentication type, and click Next.
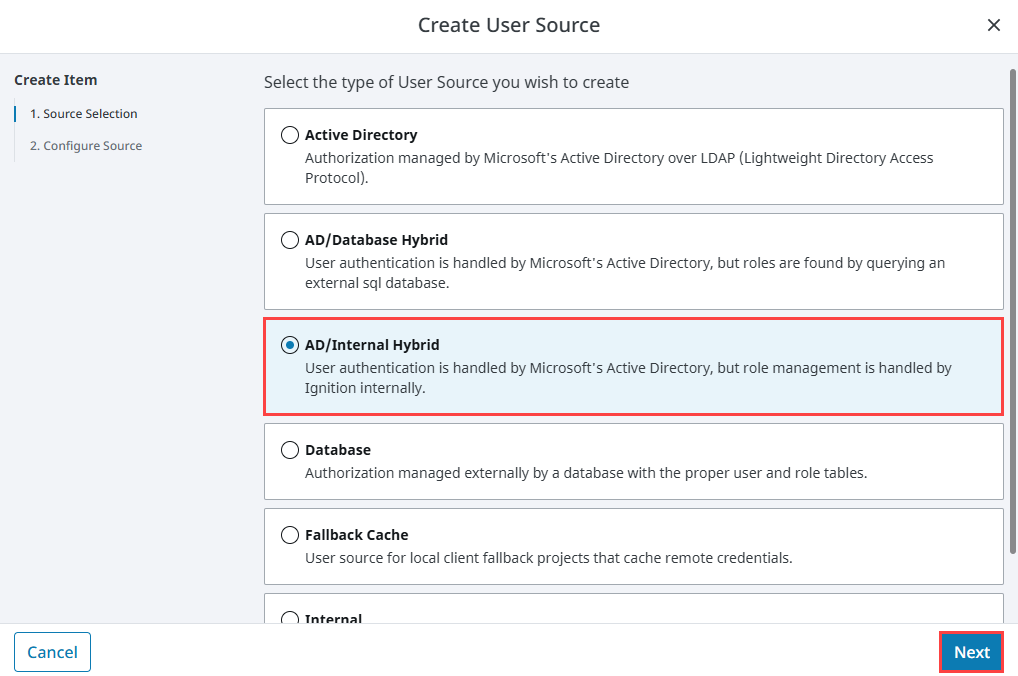
-
The Configure Source form will open. Some properties are optional depending on how you set up your profile. Details on the General Properties can be found on the User Sources page. Active Directory properties are listed in the table below.
-
Click Create User Source to save the new user source.
Active Directory Properties
| Name | Description |
|---|---|
| Domain | The Windows Domain your active Active Directory server is running on. If you aren't sure of your domain, ask your network administrator.Leave blank to set advanced properties manually. |
| Primary Domain Controller Host | The IP address or hostname of your primary domain controller. Example: "192.168.1.4" or "MainServer" |
| Primary Domain Controller Port | The port number for the primary domain controller's LDAP interface. |
| Use SSL | Disable to use "ldap://" protocol, enable to use "ldaps://" |
| List Users from Active Directory | If true, Active Directory will be queried for the list of all users. If false, users must be added manually. Default is true. |
| Populate Users On-Demand | If true, a user record will be created in the Internal Database from the AD entry of any user who successfully authenticates into Active Directory if the record does not already exist in the Internal Database at the time of authentication.When the User Source is paired with an Ignition Identity Provider, enabling this option can provide a modest performance improvement during session login. |
| Gateway Username | The login name for the Gateway to use when querying Active Directory. Used for retrieving the list of users and roles via LDAP. |
| Password | The password selections available for the Active Directory. Options include None, Embedded, and Referenced. See the Secrets Management page for more information on using Referenced passwords. |
| SSO Enabled | Whether or not to use Single-Sign-On (SSO) to authenticate AD users. Note that projects must also have this option enabled for SSO to work. Default is false.This setting was disabled and deprecated to protect against a potential security vulnerability. While the property is still visible, it cannot be enabled without setting a special system property. This is not recommended. Check out the Active Directory SSO Disabled article for more information. |
| SSO Domain | The domain that Windows users must match in order to use SSO. If blank, the main "Domain" property will be used. Not case-sensitive. |
Advanced Properties
The following table describes several configurable LDAP properties. See Microsoft's official documentation on LDAP Syntax Filters for more in-depth information about LDAP.
| Name | Description |
|---|---|
| Secondary Domain Controller Host | The IP address or hostname of your secondary domain controller (optional). Example: "192.168.1.5" or "BackupServer" |
| Secondary Domain Controller Port | The port number for the secondary domain controller's LDAP interface. Default: 389. |
| Connect Timeout | New in 8.3.2 The connect timeout in milliseconds for LDAP operations. A value smaller than one will force the LDAP operation to wait until the underlying network protocol's timeout period has been reached. Default is 0. |
| Read Timeout | The read timeout in milliseconds for LDAP operations. Default is 60,000. |
| Results Page Size | The number of entries returned per page of results in a query. Default is 1,000. |
| Username Prefix | This prefix will be prepended to the username before an Active Directory bind is attempted for authentication. |
| Username Suffix | This suffix will be appended to the username before an Active Directory bind is attempted for authentication. |
| Automatic Suffix | If this option is checked, and the suffix is left blank, then the suffix will automatically be assigned a value of @<domain>. Default is true. |
| Use prefix and suffix for Gateway username | If this option is checked, the username prefix and suffix will be applied to the Gateway username before a bind is attempted. This option is checked by default. |
| User Listing Base | The base folder to search for users under, such as DC=MyCompany,DC=com. The entire subtree under this folder will be searched using the User List Filter. Multiple subtrees can be specified by putting them in parenthesis, like so: (OU=Administrators,DC=MyCompany,DC=com)(OU=Operators,DC=MyCompany,DC=com) If you leave this blank the whole subtree of the domain controller will be searched. |
| User List Filter | The LDAP search filter used when querying for the list of all users. Should restrict the type to user. Default is (&(objectClass=user)(!(objectClass=computer))). |
| User Search Filter | The LDAP search filter to use to find a specific user. Use the placeholder 0 as a stand-in for the login name. Default is (&(objectClass=user)(sAMAccountName={0})). |
| User Name Attribute | The attribute on the User object to define the username. Default is sAMAccountName. |
| Full Name Attribute | The attribute on the User object to define the full name of the user. |
| Phone Attribute | The attribute name on the user object that represents the user's phone number. |
| Email Attribute | The attribute name on the user object that represents the user's email address. |
| SMS Attribute | The attribute name on the user object that represents the phone number that this user receives text messages on. |
| Allow Anonymous | If enabled, authentication attempts with blank passwords will be passed through to LDAP, which may choose to accept them.Caution: It is highly recommended to disable this setting unless you know it is required. AD servers may allow logging in as any user with a blank password when Security Authentication is set to “None” or “Simple” (even if a provided username does not exist in AD), which is a major security risk. |
| Security Protocol | Auto or SSL. Default is Auto. |
| Security Authentication | This property specifies how usernames and passwords are used to bind to LDAP. The following options are available:
|
| Referral | Specifies how referrals are to be processed. Possible options are:
|
SASL Properties
These settings are utilized when Security Authentication is set to SASL.
| Name | Description |
|---|---|
| Mechanism | An ordered list of space-separated mechanism names. The LDAP provider will use the first mechanism for which it finds an implementation. A blank value will leave this setting unspecified. Default is DIGEST-MD5 CRAM-MD5. |
| Realm | A realm defines the namespace from which the user is selected. A blank value will leave this setting unspecified. This setting will only be used by mechanisms which support it. Default is blank. |
| Quality of Protection | A comma-separated list of Quality-of-Protection (QoP) values, the order of which specifies the preference order. There are three well-known values: "auth" (authentication only), "auth-int" (authentication with integrity protection), and "auth-conf" (authentication with integrity and privacy protection). A blank value will leave this setting unspecified. This setting will only be used by mechanisms which support it. Default is auth-conf,auth-int,auth. |
| Protection Strength | A comma-separated list of privacy protection strength values, the order of which specifies the preference order. The three possible strength values are "low", "medium", and "high". A blank value will leave this setting unspecified. This setting will only be used by mechanisms which support it. Default is high,medium,low. |
| Mutual Authentication | Enable or disable mutual authentication. This setting will only be used by mechanisms which support it. Default is disabled. |
LDAP Attributes
| Name | Description |
|---|---|
| Attributes | A list of additional LDAP attributes to retrieve and store on the returned user.
|
