Service Security Policies
Policies can be defined for each Security Zone. Security Zones and their policies can be found within the Platform section of the Gateway under Security > Zones.
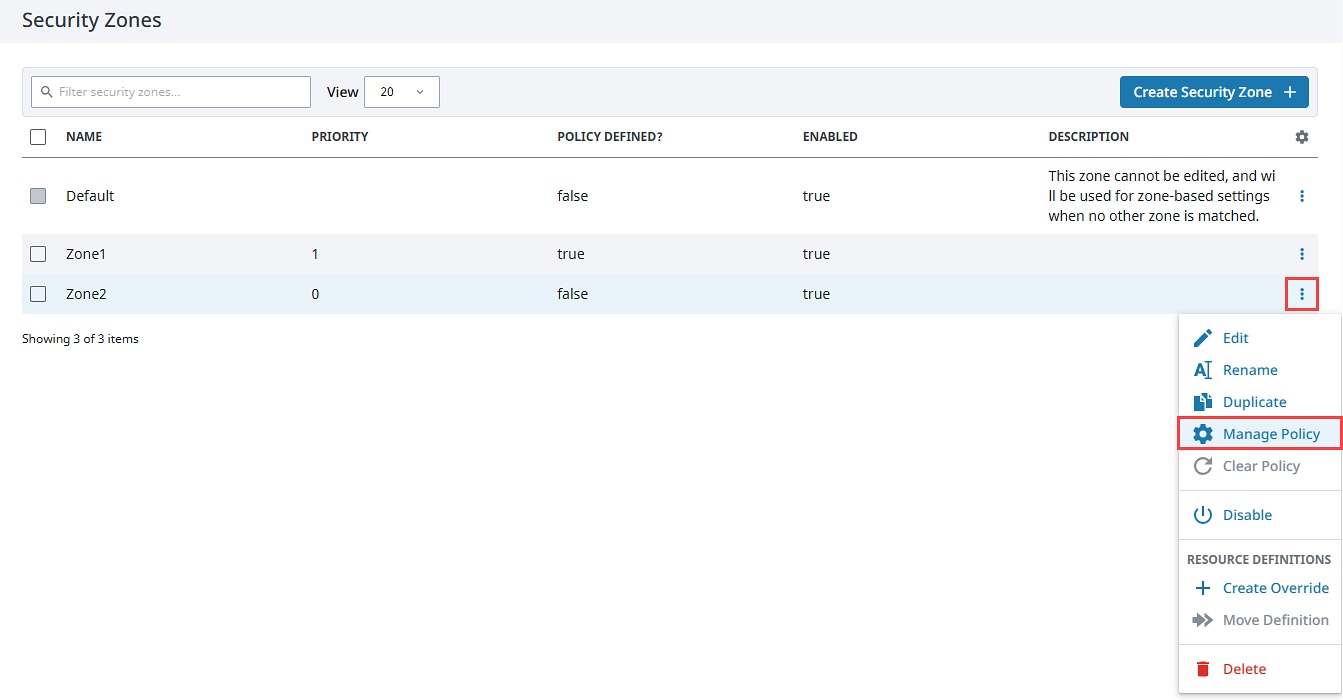
Before applying a policy, a Security Zone must exist. Once created, the Policy Defined column for the Security Zone will show as false until changes to a policy have been saved. Note that the Default Security Zone cannot be edited or have a policy applied. Expand the three dots menu for a Security Zone and select Manage Policy to define its policy.
The following services are available to define and work together to determine how the Gateway gives access to incoming Gateway connections:
- Alarm Journal Access
- Alarm Notification
- Alarm Status
- Audit Log Access
- Diagnostic Services
- EAM License Management
- History Provider Access
- Secret Provider Access
- Tag Access
If you have a single Gateway, limiting access of certain Clients to certain tags must be done by configuring the individual tag security properties.
Policy Properties
All services have the ability to completely block access with the Service Access setting. Setting this to Deny will prevent zone access to that particular information, regardless of how the rest of the options are set.
Alarm Journal Access
| Properties | Description |
|---|
| Service Access | Enables Alarm Journal access when set to Allow. |
| Default Profile Access | The default access rights for the Alarm Journal service. |
| Access Level | By default this setting will be Inherited, which will cause this specific Alarm Journal to inherit the access rights set in the Default Provider Access Level. It can also be set to No Access to block query and storage to this specific Alarm Journal. Setting it to Query Only will allow users to only query data from this Alarm Journal without any storing capability. The Query and Storage option allows users to store and query data from this Alarm Journal. It is important to note that every time a new Alarm Journal is created in the local Gateway, a new setting for this journal will be added to this Service Policy. |
Alarm Notification
| Property | Description |
|---|
| Service Access | Enables Alarm Notification access when set to Allow. |
| Access Pipeline Filter | A list of Pipelines in the current Gateway that other connections can use for alarm notification. Pipelines must be entered in the format "project_name/pipeline_name". The list is a comma separated list, and it can make use of the (*) wildcard. This setting is an inclusionary list not an exclusionary list, meaning that if there are no pipelines listed here, then all of them will be available. |
Alarm Status
| Property | Description |
|---|
| Service Access | Enables Alarm Status access when set to Allow. |
| Allow Acknowledge | Allows Gateways that fall within the zone to acknowledge alarms on the local Gateway. |
| Allow Shelving | Allow Gateways that fall within the zone to shelve alarms on the local Gateway. For this Gateway to shelve alarms on other Gateways, this must be checked on every remote Gateway. |
Audit Log Access
| Property | Description |
|---|
| Service Access | Enables Audit Log access when set to Allow. |
| Default Profile Access | The default access rights for the Audit Profile service. |
| Access Level | By default this setting will be set to Inherited, which will cause this specific Audit Profile to inherit the access rights set in the Default Provider Access Level. It can also be set to No Access to block query and storage to this specific Audit Profile. Setting it to Query Only will allow users to only query data from this Audit Profile without any storage ability. The Query and Storage option allows users to store and query data from this Audit Profile. Just like with Alarm Journals, it is important to note that every time a new Audit Profile is created in the local Gateway, a new setting for this profile. |
Diagnostic Services
| Property | Description |
|---|
| Service Access | Enables Diagnostic Services access when set to Allow. |
| Gateway Network Crawler | If checked, the Gateway will allow a remote Gateway to "crawl" the Gateway Network routes and return diagnostic information about the Gateways along the routes. Returned information includes platform version and edition, and connectivity statistics (such as ping time). |
EAM License Management
| Property | Description |
|---|
| Service Access | Enables EAM License access when set to Allow. |
| Agent Leased License Management | Applies to EAM Controller only. If checked, an EAM Agent can forward leased license activations and renewals to this Gateway. This Gateway will then contact the licensing server and send the results back to the agent Gateway. |
History Provider Access
| Property | Description |
|---|
| Service Access | Enables History Provider access when set to Allow. |
| Default Profile Access | The default access rights for Tag History. It is not recommended to set the Default Access Profile to Inherited since all new History Providers will automatically get added to the Service Policy with an Access Level setting of inherited. Instead, it may be beneficial to set the Default Profile Access to be either Read Only or No Access so that an added History Provider does not accidentally get storage rights. |
| Access Level | By default this setting will be set to Inherited, which will inherit the Default Profile Access rights. If set to Query and Storage, connections in the current zone can both run queries and store against the Tag History Provider. Query Only will only allow the zone to query out history data, but not store it. No Access will completely block access to the History Provider. |
Secret Provider Access
New in 8.3.3
| Property | Description |
|---|
| Service Access | Enables Secret Provider access when set to Allow. |
| Default Provider Access Level | The default access rights for Secret Providers. |
| Access Level | This setting will appear for each Secret Provider configured, listed by name. By default, it is set to Inherited, which will inherit the Default Provider Access Level value. |
Tag Access
| Property | Description |
|---|
| Service Access | Enables Tag Provider access when set to Allow. |
| Default Profile Access Level | Sets the default access rights for realtime Tag Providers. It is not recommended to set the Default Access Profile to Inherited. |
| Trust Remote Security Levels | Allows users to opt into trusting the Security Levels of remote Gateway users when remote Gateways read, write, and subscribe to local tags. If checked, Security Levels passed from the remote Gateway will be used for determining access to tags on the local Gateway. If unchecked, the remote Gateway's Security Zones and the impersonation role will be used as the Security Levels. |
| Impersonation Role Name | Allows you to specify a role name to use when writing to a tag from an incoming Gateway Network connection (from the selected zone). |
| Access Level | An Access Level setting will exist for each Tag Provider configured in the local Gateway, as well as an additional one for System tags. By default the level is set to Inherited, which will inherit the access rights set in the Default Provider Access Level. Other level settings include ReadWriteEdit, which will allow connections in the current zone to read, write to, and edit the tags in that provider; ReadWrite, which allows the zone to read and write to tags; and ReadOnly, which allows the zone to only read the tags. It also can be set to None, which will prevent the zone from interacting with the Tag Provider altogether. |
Default Security Zone�
While the Default Security Zone may not have a custom policy defined, it is configured to allow Alarm Acknowledgment, query only for History Provider Access, read only for Tag Access, and not to include Notification Pipelines. This means that if a remote Tag Provider is set up on a remote Gateway, and the local Gateway has not changed the default service settings, the remote Gateway will have read only access to the Tag History Provider. This can be changed by overriding the Default Security Zone or by creating new Security Zones with custom policies. Once a policy has been defined on a zone, it will automatically take precedence over the default policy.
