Gateway and Gateway Network Parameters
Gateway Parameters
Gateway Security HTTP Headers and Configuration
Gateway security headers system properties and default settings are listed below. These parameters impact Perspective sessions, as well as any pages hosted on Ignition's web server.
Strict Transport Security
The following system properties interact with the Strict-Transport-Security header. Enabling the header involves setting the Dignition.https.sts.maxAge system property to a non-zero value. By default, the header is disabled.
| System Property | Description |
|---|---|
-Dignition.https.sts.maxAge | Sets the maximum age of the Strict Transport Security header. The value should be set to an integer, representing a number of seconds the browser should remember that a site is only to be accessed using HTTPS. Setting this to a number less than zero will disable the header altogether. |
-Dignition.https.sts.includeSubDomains | Applies the includeSubDomains parameter. Expects a boolean value. If omitted, defaults to false. |
-Dignition.https.sts.preload | New in 8.1.5 This parameter allows websites to tell the browser to only connect using HTTPS. It can be set to true or false to enable or disable the preload directive of the Strict-Transport-Security header. If omitted, defaults to false. |
wrapper.java.additional.1=-Dignition.https.sts.maxAge=31536000
wrapper.java.additional.2=-Dignition.https.sts.includeSubDomains=false
wrapper.java.additional.3=-Dignition.https.sts.preload=true
Referrer Policy
The following system properties interact with the Referrer-Policy header. By default, the header is enabled with a value of strict-origin-when-cross-origin.
| System Property | Description |
|---|---|
-Dignition.http.header.referrer_policy.enabled | Allows you to enable or disable the Referrer-Policy header. Expects a true or false value. |
-Dignition.http.header.referrer_policy.value | Sets the value of the Referrer-Policy. |
wrapper.java.additional.1=-Dignition.http.header.referrer_policy.enabled=true
wrapper.java.additional.2=-Dignition.http.header.referrer_policy.value=strict-origin-when-cross-origin
X Content Type Options
The following system properties interact with the X-Content-Type-Options header. By default, the header is enabled with a value of nosniff.
| System Property | Description |
|---|---|
-Dignition.http.header.x_content_type_options.enabled | Allows you to enable or disable the X-Content-Type-Options header. Expects a true or false value. |
-Dignition.http.header.x_content_type_options.value | Determines the value of the X-Content-Type-Options. |
wrapper.java.additional.1=-Dignition.http.header.x_content_type_options.enabled=true
wrapper.java.additional.2=-Dignition.http.header.x_content_type_options.value=nosniff
X Frame Options
The following system properties interact with the X-Frame-Options header. By default, the header is enabled with a value of SAMEORIGIN.
If you're embedding a Perspective session inside an iframe from another origin and it stops working after upgrade, then you may need to modify the X-Frame-Options header.
| System Property | Description |
|---|---|
-Dignition.http.header.x_frame_options.enabled | Enables or disables the X-Frame-Options header. |
-Dignition.http.header.x_frame_options.value | Determines the value of the X-Frame-Options header. |
wrapper.java.additional.1=-Dignition.http.header.x_frame_options.enabled=true
wrapper.java.additional.2=-Dignition.http.header.x_frame_options.value=SAMEORIGIN
X XSS Protection
The following system properties interact with the X-XSS-Protection header. By default, the header is enabled with a value of 1; mode=block.
| System Property | Description |
|---|---|
-Dignition.http.header.x_xss_protection.enabled | Enables or disables the X-XSS-Protection header. |
-Dignition.http.header.x_xss_protection.value | Determines the value of the X-XSS-Protection header. |
wrapper.java.additional.1=-Dignition.http.header.x_xss_protection.enabled=true
wrapper.java.additional.2=-Dignition.http.header.x_xss_protection.value=1; mode=block
Thread Pool Counts
In some testing and troubleshooting scenarios, it may be required to increase thread pool counts from their default settings.
While there is no limit on how high thread pool counts can be increased, be aware that resource usage such as CPU and RAM will also increase.
Tag Value Change Scripts
The following system properties allow you to increase the tag value change script thread pool count and queue size. By default, the thread pool count is set to 3 and the queue size is set to 5.
| System Property | Description |
|---|---|
-Dignition.tags.scriptthreads | Sets the tag event script thread count. The value should be an integer, representing the thread count. |
-Dignition.tags.scriptqueuemaxsize | Sets the tag event script queue size. The value should be an integer, representing the queue size. |
wrapper.java.additional.1=-Dignition.tags.scriptthreads=5
wrapper.java.additional.2=-Dignition.tags.scriptqueuemaxsize=10
Query Tags
The following system property allows you to increase the thread pool count of ignition.tags.db_tag_threads. By default, the thread pool count is set to 3.
| System Property | Description |
|---|---|
-Dignition.tags.db_tag_threads | Sets the Query tag thread pool count. The value should be an integer, representing the thread pool count. |
wrapper.java.additional.1=-Dignition.tags.db_tag_threads=10
Expression Tags
The following system property allows you to increase the thread pool count of ignition.tags.expressionthreads. By default, the thread pool count is set to 3.
| System Property | Description |
|---|---|
-Dignition.tags.expressionthreads | Sets the Expression tag thread pool count. The value should be an integer, representing the thread pool count. |
wrapper.java.additional.1=-Dignition.tags.expressionthreads=10
Transaction Groups
The following system property allows you to increase the thread pool count of ignition.sqlbridge.maxthreads. By default, the thread pool count is set to 5.
| System Property | Description |
|---|---|
-Dignition.sqlbridge.maxthreads | Sets the thread pool count for transaction groups. The value should be an integer, representing the thread pool count. |
wrapper.java.additional.1=-Dignition.sqlbridge.maxthreads=10
HTTP Client Manager
The following system properties interact with the platform's HTTP Client. These settings allow you to configure how the IdP system and Perspective's HTTP Bindings parse cookies, handle idle HTTP connections, and respect proxy settings.
| System Property | Description |
|---|---|
-Dignition.http.client.manager.cookieSpec | Controls the cookie parsing behavior of the HTTP Client. This system property may take one of the following values:
|
-Dignition.http.client.manager.socket.keepalive | When set to true, HTTP connections issued from the HTTP Client will set the SO_KEEPALIVE flag on the underlying socket, enabling keepalive. Enabling keepalive maintains a connection between a client and the server, reducing the number of TCP and SSL/TLS connection requests. You must also enable and configure keepalive settings on the OS running the Gateway. See KeepAlive Configuration. |
-Dignition.http.client.manager.pool.idleConnectionCheckInterval | An integer representing the duration in seconds between each check for idle connections. This value is ignored when maxIdleConnectionTime is less than or equal to zero. If this value is undefined or less than or equal to zero, then the interval is set to match maxIdleConnectionTime. |
-Dignition.http.client.manager.pool.maxIdleConnectionTime | An integer representing the number of seconds that connections in the HTTP connection pool may be idle (i.e. no data is sent or received on the socket) before it is evicted and closed. If set to any number less than or equal to zero or undefined, idle connection eviction will be disabled. |
-Dignition.http.client.manager.proxy.enabled | If set to true, the HTTP Client will respect the JVM's system default proxy settings. Default value if undefined is false. |
wrapper.java.additional.1=-Dignition.http.client.manager.cookieSpec=standard-strict
wrapper.java.additional.2=-Dignition.http.client.manager.socket.keepalive=true
wrapper.java.additional.3=-Dignition.http.client.manager.pool.idleConnectionCheckInterval=60
wrapper.java.additional.4=-Dignition.http.client.manager.pool.maxIdleConnectionTime=300
wrapper.java.additional.5=-Dignition.http.client.manager.proxy.enabled=true
KeepAlive Configuration Examples
KeepAlive Configuration for Windows
The following example involves modifying a registry value on Windows. incorrect registry configurations can cause serious problems and impact your server's performance. For information on how to back up and restore the registry in Windows, click here.
In this example, we'll add the fllowing parameters to our registry:
| Name | Data Type | Range | Default Value |
|---|---|---|---|
| KeepAliveTime | REG_DWORD | 0x1–0xFFFFFFFF (milliseconds) | 0x6DDD00 (7,200,000 milliseconds = 2 hours) |
| KeepAliveInterval | REG_DWORD | 0x1–0xFFFFFFFF (milliseconds) | 0x3E8 (1,000 milliseconds = 1 second) |
-
Navigate to \HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters.
-
If parameters for \KeepAliveTime and \KeepAliveInterval do not exist, create them.
-
Click Edit>New>DWORD (32-bit) Value.
-
Open the Registry Editor.
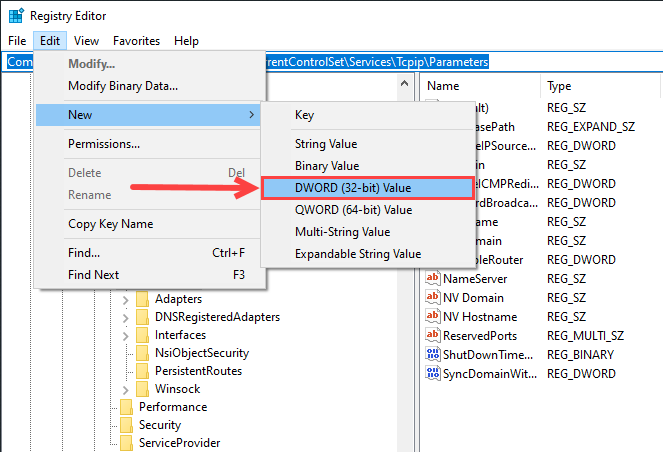
-
Enter the values listed on the table above this example (KeepAliveTime and KeepAliveInterval)
-
Exit the Registry Editor.
-
Restart the computer for changes to take effect.
KeepAlive Configuration for Linux
For Linux systems, there are three parameters to change:
| Name | Default Value |
|---|---|
| tcp_keepalive_time | 7200 (seconds) |
| tcp_keepalive_intvl | 75 (seconds) |
| tcp_keepalive_probes | 9 (number of probes) |
- Edit /etc/sysctl.conf:
# vi /etc/sysctl.conf - Add the following settings:
net.ipv4.tcp_keepalive_time = #newvaluenet.ipv4.tcp_keepalive_intvl = #newvaluenet.ipv4.tcp_keepalive_probes = #newvalue
The following system property will configure Ignition to use IPv4 sockets only.
| System Property | Description |
|---|---|
-Djava.net.preferIPv4Stack | Configures Ignition to use only IPv4 sockets when this property is set to true. |
Maximum Form Size
By default, the maximum size is kept low on the default installation to prevent DoS attacks. We do not recommend changing this, especially so if the Gateway isn't in a closed network.
This parameter allows you limit the amount of data that can be posted back from a browser or other client, to the Gateway. Generally, this is useful to increase the maximum size for Web Dev POST requests. More information about this parameter can be found in Jetty's documentation.
wrapper.java.additional.1=-Dorg.eclipse.jetty.server.Request.maxFormContentSize=2000000
Internal Database
Connection Timeout
The default maximum time that the Gateway will wait for a connection to an internal database is 30 seconds. This parameter allows you to override this setting and increase the maximum wait time.
wrapper.java.additional.1=-Dignition.internalDbMaxWait=60000
Internal Database VACUUM Operation
A VACUUM operation is executed against the internal database upon Gateway startup by default. This operation reclaims unused disk space, trimming down on both the time it takes for auto-backups to complete, as well as the overall size of the internal database itself. This action can be disabled by using the following parameter.
wrapper.java.additional.1=-Dignition.skipConfigDbVacuum=true
Internal Database Legacy Tag Cleanup
Upon Gateway startup, you can conduct a cleanup task on old 7.X.X SQLTAG tables. This helps to reduce bloated internal databases, save disk space, and potentially improve Gateway performance. Using the following parameter will opt the Gateway in for performing this cleanup task.
wrapper.java.additional.1=-Dignition.tags.cleanupLegacyTagTables=true
Internal Database Project Table Cleanup
Upon Gateway startup, a cleanup task is conducted on old 7.X.X project tables. This helps to trim down internal databases, providing more space for other operations, and may improve Gateway performance. The following parameter will allow you to skip this cleanup operation.
wrapper.java.additional.1=-Dignition.projects.skipProjectRecordTableCleanup=true
Hosted Launcher Installers
Normally, each Ignition Gateway includes files for the various launchers. When you download a launcher from a Gateway, it simply streams its local launcher files. However, you can override this behavior, causing the Gateway to ignore it's local launcher files and instead download launchers from the internet. This is an uncommon configuration for most cases, as it was devised primarily to aid with systems where memory limitations are strict (such as physical devices that include preinstalled Ignition Gateways).
Enabling Hosted Launchers
The following parameter (and value) enables the use of hosted launchers. While enabled, the Gateway will only ever attempt to retrieve the hosted launchers, meaning it will ignore the local launcher files.
wrapper.java.additional.1=-Dignition.hostedLaunchers=true
Hosted Launcher Version
By default, enabling Hosted Launchers will cause the Gateway to retrieve launchers version appropriate launchers: 8.0.0 launchers for 8.0.0 Gateways, 8.1.0 launchers for 8.1.0 Gateways, etc.
The parameter below can be used to explicitly state which launcher version to retrieve. Generally, this is not recommended, but can potentially be useful if you're looking for a specific launcher version. It requires that -Dignition.hostedLaunchers is set to "true".
wrapper.java.additional.1=-Dignition.hostedLauncherVersion=8.1.0
Automatic Thread Dump Sample Rate
The following parameter can be used to override the default sample rate of 1 second for Automatic Thread Dumps. The time is set in milliseconds, and the minimum time setting is 500ms.
wrapper.java.additional.1=-Dignition.automaticThreadDump.sampleRate=5000
Ignition Edition
You can specify which edition of Ignition a Gateway should be set to with the parameter demonstrated below.
wrapper.java.additional.1=-Dedition=standard
Ignition Gateway Licenses are matched to a specific edition. Changing the edition of an Ignition Gateway that is already licensed can result in the license becoming invalidated. It's recommended that you unactivate a license on a gateway before changing its edition.
Values
- Standard Ignition -
standard - Ignition Edge -
edge - Ignition Maker -
maker
Loading Unsigned Modules - Developer Mode
Normally, an Ignition Gateway will not allow unsigned module to be installed. This restriction can be disabled with the flag below. This is normally done in cases where a user is developing a custom module, and wants to install it without having the module signed.
wrapper.java.additional.1=-Dignition.allowunsignedmodules=true
Project Directory Scan Rate
This setting dictates how often the Ignition Gateway will scan its project directory for changes. As of Ignition 8.1.0 this was changed to a 300 second rate (from a 10 seconds rate), but it can be configured. This is useful in cases where project files are being modified from external sources and the gateway needs to be aware of theses changes in a more timely manner. The argument below expects an integer, which represents a number of seconds.
wrapper.java.additional.1=-Dignition.projects.scanFrequency=100
Ignored Project Directory Files
This setting allows users to specify a list of folders in the project directory that the Ignition Gateway will ignore when scanning for changes. By default, the Gateway will ignore changes to any files located within folders with the name ".git", ".svn", or ".hg". The argument below expects a list of additional folders to ignore, using the ':' character as a file separator.
wrapper.java.additional.1=-Dignition.projects.ignoredFiles=Folder1:Folder2:Folder3
By specifying a folder to ignore, note that any folder within the data/projects folder with the same name will be excluded, including any projects with that name. For example, if you exclude a folder called "test" and your project name is also "test" the project will be excluded as well.
Redundant Alarm Runtime Limit
In redundant systems, both alarm event and alarm shelf items wait in separate queues on the active node before they're transferred to the inactive node. Normally the active node sends recently changed alarm events and shelve events to the inactive node as they occur. However if the queue becomes full the active node will pause this behavior and send a full transfer to the inactive node, ensuring that the state of events on the inactive node is accurate.
| System Property | Description |
|---|---|
-Dalarm.redundancy.runtimeupdates.max | Determines the maximum size of the alarm events queue. Defaults to 2,000,000 if omitted. |
-Dalarmshelf.redundancy.runtimeupdates.max | Determines the maximum size of the alarm shelf queue. Defaults to 2,000,000 if omitted. |
wrapper.java.additional.1=-Dalarm.redundancy.runtimeupdates.max=1000000
wrapper.java.additional.2=-Dalarmshelf.redundancy.runtimeupdates.max=1000000
Web Server
The following parameters are used to configure Ignition's default settings for web requests that are not configured in some other, more specific manner, such as Perspective Route Handling. These settings usually do not need to be modified, but a higher value may help mitigate issues on very busy systems.
| System Property | Description |
|---|---|
-Dignition.routes.defaultConcurrency | Determines the number of concurrent sessions allowed to acquire a lock per webserver route. The lock must be acquired within two seconds of an incoming request, or the request will return an error. Default is 5. |
-Dignition.routes.defaultRequestTimeout=xxxx | New in 8.1.38 The route group concurrency timeout value. Increasing this value may help mitigate timeout and error 503 issues. Default is 2000 milliseconds (2 seconds) |
wrapper.java.additional.1=-Dignition.routes.defaultConcurrency=5
wrapper.java.additional.2=-Dignition.routes.defaultRequestTimeout=2000
JX Browser User Directories
These parameters allow users to specify a direct user data directory other than the default directory. This change will apply to both Designers, Perspective sessions, and the Vision Web Browser Component, regardless of the user's operating system.
| System Property | Description |
|---|---|
-Dignition.jxBrowser.userDataDir.browser | Specifies the user data directory to use for the Vision Web Browser Component. |
-Dignition.jxBrowser.userDataDir.perspective | Specifies the user data directory to use for a Perspective session. |
wrapper.java.additional.1=-Dignition.jxBrowser.userDataDir.browser=C:\Users\ignitionUser\AppData\Local\Temp\2\UserData\3e2704e3
wrapper.java.additional.2=-Dignition.jxBrowser.userDataDir.perspective=C:\Users\ignitionUser\AppData\Local\Temp\2\UserData\4f3815f4
Gateway Diagnostic Bundle Export Memory Dump
The following parameter enables a memory dump as part of the diagnostic bundle export feature.
| System Property | Description |
|---|---|
-Dignition.diagnostic-bundle.enable-memory-dump | Enables or disables a memory dump as part of the diagnostic bundle. Expects either "true" or "false". Defaults to "false". |
wrapper.java.additional.1=-Dignition.diagnostic-bundle.enable-memory-dump=true
SMTP Email Notifications
The following parameter allows users to define send behavior when an invalid notification email is present for the system.net.sendEmail() function.
| System Property | Description |
|---|---|
-Dignition.smtp.sendpartial | If the value is set to true, email notifications are sent to the valid emails provided for that user and an exception is logged for the failed emails. If set to false, no emails are sent if any of the provided emails are invalid. The default value is set to true. |
wrapper.java.additional.1=Dignition.smtp.sendpartial=true
Restore File TTL
The following parameter configures the time-to-live (TTL) for restore files used during backup and restore processes, including redundancy. This setting determines how long restore files are retained before being automatically deleted.
| System Property | Description |
|---|---|
-Dignition.redundancy.restoreFileTTL | Sets the TTL for restore files used in both redundancy and general backup/restore operations. The value should be an integer, representing the number of minutes the file will be retained. The default value is 20 minutes. |
wrapper.java.additional.1=-Dignition.redundancy.restoreFileTTL=20
Gateway Network Parameters
Proxy Depth
By default, Gateway remote providers can only "hop" two Gateways away. For example, assume the numbers below represent Gateways, which are all connected over a Gateway Network.
1 -- 2 -- 3 -- 4
Normally, Gateway 1 only has access to Gateway 2 and 3. Gateway 4 is too far away. However this can be changed by adding the following to Gateway 1's configuration file:
wrapper.java.additional.1=-Dignition.gan.maxproxydepth=3
The Allow Proxying setting must be enabled for requests to be forwarded in this manner.
Ping Thread Count
The following system property allows you to increase the ping thread pool count to reduce the connection reconnect time if multiple outgoing connections are faulted. By default, the count is set to 3 and with a 10 second timeout. For example, if no adjustments are made and there are 15 faulted outgoing connections, there would be about a minute delay for new incoming connections.
| System Property | Description |
|---|---|
-Dignition.metro.pingexecutor.threads | Sets the ping thread count. The value must be an integer. |
wrapper.java.additional.1=-Dignition.metro.pingexecutor.threads=10
Gateway Network Queue Timeout
The Long Wait Queue timeout and Proxy Queue timeout can be adjusted if necessary for slower connections. These settings will mostly apply to EAM, but can also apply for more general GAN instances such as a GWBK transferring from a redundant master to a backup.
| System Property | Description |
|---|---|
-Dmetro.queues.proxyQueue.timeoutSecs | By default, the Proxy Queue will timeout after 60 minutes. This can be adjusted by setting the system property shown. |
-Dmetro.queues.longWaitQueue.timoutSecs | This parameter will adjust the Long Wait Queue timeout setting. The Long Wait Queue defaults to handle messages that take up to an hour to deliver if left unchanged. Note: The longWaitQueue system property was implemented without the "e" in timeout. Be sure to spell it as shown in the System Property field when using. |
EAM Timeout
The following system properties interact with EAM. These settings allow you to configure the timeout settings for various possible actions in EAM.
| System Property | Description |
|---|---|
-Dignition.eam.task.collectBackup.transferTimeout | New in 8.1.17 By default, the EAM Collect Backup task will timeout if the Agent takes longer than 60 minutes to transfer the backup to the Controller over the Gateway Network. This setting can be adjusted by adding the aforementioned parameter, which expects an integer value in milliseconds. |
-Dignition.eam.freeSpace.timeout.millis | New in 8.1.18 This parameter will allow for adjusting the timeout setting that checks if there is sufficient free space to perform the EAM Controller's save operations. Expects an integer value in milliseconds. Default value is 10,000 milliseconds (10 seconds). |
-Dws.handoff.timeout | New in 8.1.29 By default, EAM tasks that need to send a large file through a proxy Gateway timeout after 60 minutes. This value can be adjusted by setting the handoff timeout system property integer value, in seconds, on the proxy Gateway. |
HTTPS Settings
The following system properties will either include or exclude specified cipher suites for the Gateway Network port 8060. For including or excluding cipher suites for port 8043, refer the the Web Server Settings page.
| System Property | Description |
|---|---|
-Dciphers | Lists included cipher suites for connections using SSL/TLS for port 8060. |
-DexcludedCiphers | Lists excluded cipher suites for connections using SSL/TLS for port 8060. |
# Make sure to separate listed cipher suites with a comma.
wrapper.java.additional.X=-Dciphers=TLS_DHE_DSS_WITH_AES_128_CBC_SHA256,TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
wrapper.java.additional.X=-DexcludedCiphers=TLS_AES_128_GCM_SHA256,TLS_AES_256_GCM_SHA384,TLS_CHACHA20_POLY1305_SHA256,TLS_DHE_DSS_WITH_AES_128_CBC_SHA